The Rise of Info Stealer Malware: A Growing Threat to Businesses
Stealer malware, or information-stealing malware, is a type of malicious software designed to gather sensitive information typically targeting personal, financial, or business-related data. The data collected could include passwords, financial information, corporate data, and personal identification details. Once installed, this malware operates discreetly, often without triggering any noticeable alarms, making it particularly dangerous. The functionality… Continue reading The Rise of Info Stealer Malware: A Growing Threat to Businesses
Will AI Kill the Pen Testing Star
Those who use the different AI support technology available, are seeing a trend, that the results, generally speaking, produced by the tools are getting better every month. There is still the old computing issue of garbage in, garbage out, but as we learn to better seed the bots and the bots learn what data we… Continue reading Will AI Kill the Pen Testing Star
How AI is Impacting Cybersecurity and Penetration Testing
In the era of rapid technological advancement, the proliferation of AI platforms is revolutionising the way we interact with digital information, enhancing productivity, and streamlining decision-making processes. However, this same technology, designed to simplify and enrich our lives, is being weaponized by hackers and bad actors. These individuals exploit the capabilities of AI to orchestrate… Continue reading How AI is Impacting Cybersecurity and Penetration Testing
Penetration Testing: Unravelling the Anatomy
In an era where the digital landscape is riddled with threats and vulnerabilities, organisations must be proactive in safeguarding their information systems. Penetration testing, often known as ethical hacking or pen testing, is a vital practice in the world of cybersecurity. It allows organisations to assess their security posture, identify vulnerabilities, and fortify their defences.… Continue reading Penetration Testing: Unravelling the Anatomy
What is the best AI ChatBot to use for Penetration Testing (Part One)
Our earlier Red Cursor blog articles on how to use ChatGPT to aid with Penetration Testing have given our team cause to pause and wonder, what is the best AI Chatbot for aiding in pen testing? Unsurprisingly, our research has led to many more questions, so for a bit of foreshadowing, we will need to… Continue reading What is the best AI ChatBot to use for Penetration Testing (Part One)
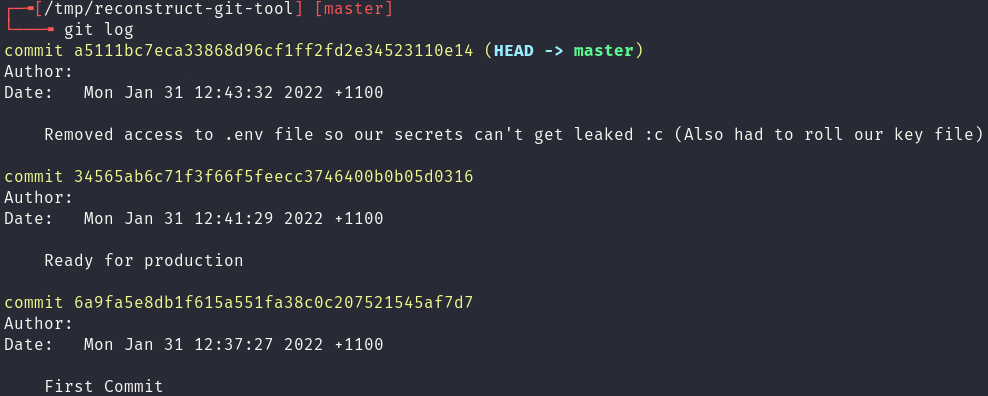
Exploring .git leaks
One of the most common mistakes a developer can make, especially when working with technologies like Docker, is copying their .git folder into the web root of their website. This vulnerability usually leads to leaked secrets, credentials and source code. In this blog post Red Cursor will: identify the existence of a .git folder on… Continue reading Exploring .git leaks
Penetration Testing and Web Application Firewalls
A Web Application Firewall (WAF) is a defence-in-depth mitigation against common web attacks by monitoring and filtering HTTP traffic. WAFs work by analysing the plaintext content of HTTP messages between the client and server to determine if the given message is malicious. If it’s deemed to be malicious, the WAF stops the message from reaching… Continue reading Penetration Testing and Web Application Firewalls
Black Box Penetration Testing
Penetration testing – or pen-testing as we colloquially call it – is a crucial component to a robust security programme in any organisation. As management, it’s critical you understand where pen-testing fits into your programme and what it can do for your organisation. Equally important is what it can’t do, and how the different “flavours”… Continue reading Black Box Penetration Testing
When it all goes wrong on AWS – how an SSRF can lead to full control of your EC2 infrastructure
AWS is an incredibly powerful cloud platform that enables businesses to quickly and efficiently deploy a wide range of software and services to end users. This feature-rich environment does of course increase the attack surface that bad actors have to exploit, especially when combined with lax configurations and poorly designed APIs. In this blog post,… Continue reading When it all goes wrong on AWS – how an SSRF can lead to full control of your EC2 infrastructure
Dumping Active Directory Credentials
All Active Directory user account password hashes are stored inside the ntds.dit database file on the Domain Controllers. However, if you have ever tried copying the file, you’ll probably have received the following error message. Well as it turns out, the LSASS process has already opened the file, and when it called CreateFileW to open… Continue reading Dumping Active Directory Credentials