Using Mimikatz
OverPass-the-Hash Mimikatz can perform the well-known operation “OverPass-The-Hash” to run a process under the security context of another account’s credentials. This is extremely powerful and should not be underestimated. Behind the scenes, Mimikatz requests a Kerberos ticket from the domain controller using the NTLM hash provided. The Kerberos ticket allows authentication to Kerberos services within… Continue reading Using Mimikatz
Penetration Testing Frequently Asked Questions
When is penetration testing required? You have developed an application (in-house or outsourced), purchased an application (commercial off the shelf product), or purchased a software as a service (SaaS) and have concerns or compliance requirements regarding the security of the application or data stored. These concerns can be broadly categorised, in that an adversary or… Continue reading Penetration Testing Frequently Asked Questions
Exploring .git leaks
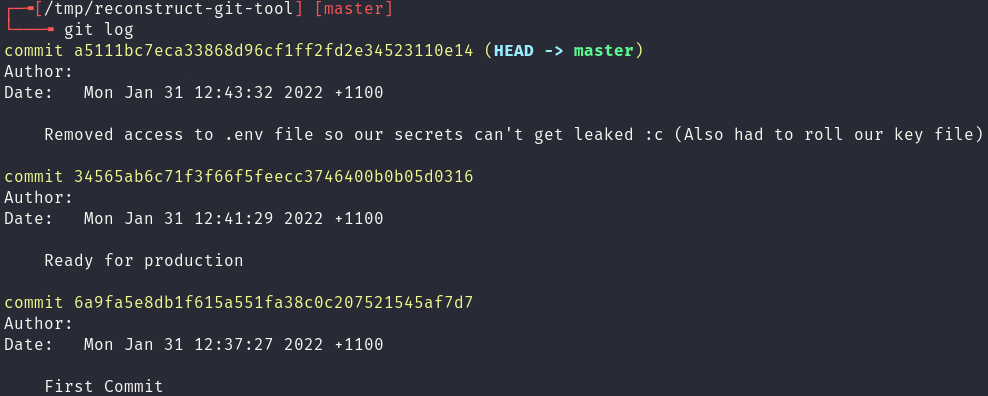
One of the most common mistakes a developer can make, especially when working with technologies like Docker, is copying their .git folder into the web root of their website. This vulnerability usually leads to leaked secrets, credentials and source code. In this blog post Red Cursor will: identify the existence of a .git folder on… Continue reading Exploring .git leaks
Why is penetration testing required?
What is Penetration Testing? Penetration testing, whether it be black box or white box, is a form of risk assessment that aims to identify cybersecurity vulnerabilities and risks within a system. Usually, security is considered a balancing act between confidentiality, integrity and availability. Confidentiality being the ability of the system to keep personal information secret.… Continue reading Why is penetration testing required?
Penetration Testing and Web Application Firewalls
A Web Application Firewall (WAF) is a defence-in-depth mitigation against common web attacks by monitoring and filtering HTTP traffic. WAFs work by analysing the plaintext content of HTTP messages between the client and server to determine if the given message is malicious. If it’s deemed to be malicious, the WAF stops the message from reaching… Continue reading Penetration Testing and Web Application Firewalls
White Box Penetration Testing
There are two main ways to conduct penetration testing: black box and white box. Both provide different approaches to the methodology and require different levels of interaction from the client. White box can often return more findings while improving the tester’s efficiency. We’ve already covered black box testing in the first part of this two-part… Continue reading White Box Penetration Testing
Black Box Penetration Testing
Penetration testing – or pen-testing as we colloquially call it – is a crucial component to a robust security programme in any organisation. As management, it’s critical you understand where pen-testing fits into your programme and what it can do for your organisation. Equally important is what it can’t do, and how the different “flavours”… Continue reading Black Box Penetration Testing
Kubernetes Security Part 1 – Creating a test Kubernetes Cluster with kubeadm
As enterprise moves towards Cloud Computing, large technologies and platforms, such as AWS, contain complex infrastructure that is susceptible to complex security concerns, and Kubernetes clusters are no exception. Red Cursor has started testing applications that are running as containers within these clusters and having access to a running, reproducible test environment is becoming vital… Continue reading Kubernetes Security Part 1 – Creating a test Kubernetes Cluster with kubeadm
When it all goes wrong on AWS – how an SSRF can lead to full control of your EC2 infrastructure
AWS is an incredibly powerful cloud platform that enables businesses to quickly and efficiently deploy a wide range of software and services to end users. This feature-rich environment does of course increase the attack surface that bad actors have to exploit, especially when combined with lax configurations and poorly designed APIs. In this blog post,… Continue reading When it all goes wrong on AWS – how an SSRF can lead to full control of your EC2 infrastructure
Dumping Active Directory Credentials
All Active Directory user account password hashes are stored inside the ntds.dit database file on the Domain Controllers. However, if you have ever tried copying the file, you’ll probably have received the following error message. Well as it turns out, the LSASS process has already opened the file, and when it called CreateFileW to open… Continue reading Dumping Active Directory Credentials