Capturing and Relaying NTLM Authentication: Methods and Techniques
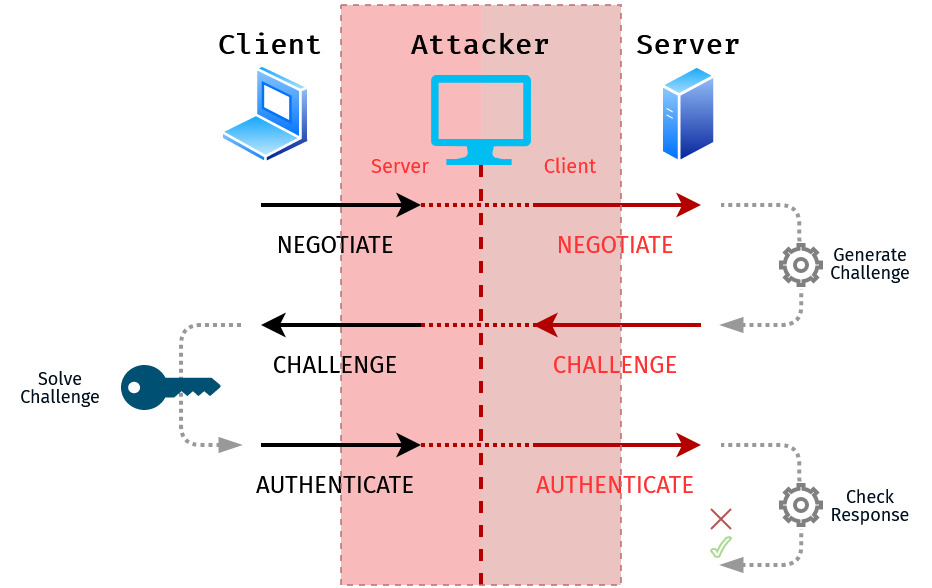
This blog post will provide an overview of the methods available to force NTLM authentication to a rogue server, and capture or relay the credential material. These attacks can be leveraged to escalate privileges within an Active Directory domain environment. I like to look at these attacks as having 3 stages which are: Positioning a… Continue reading Capturing and Relaying NTLM Authentication: Methods and Techniques
Game Over Privileges
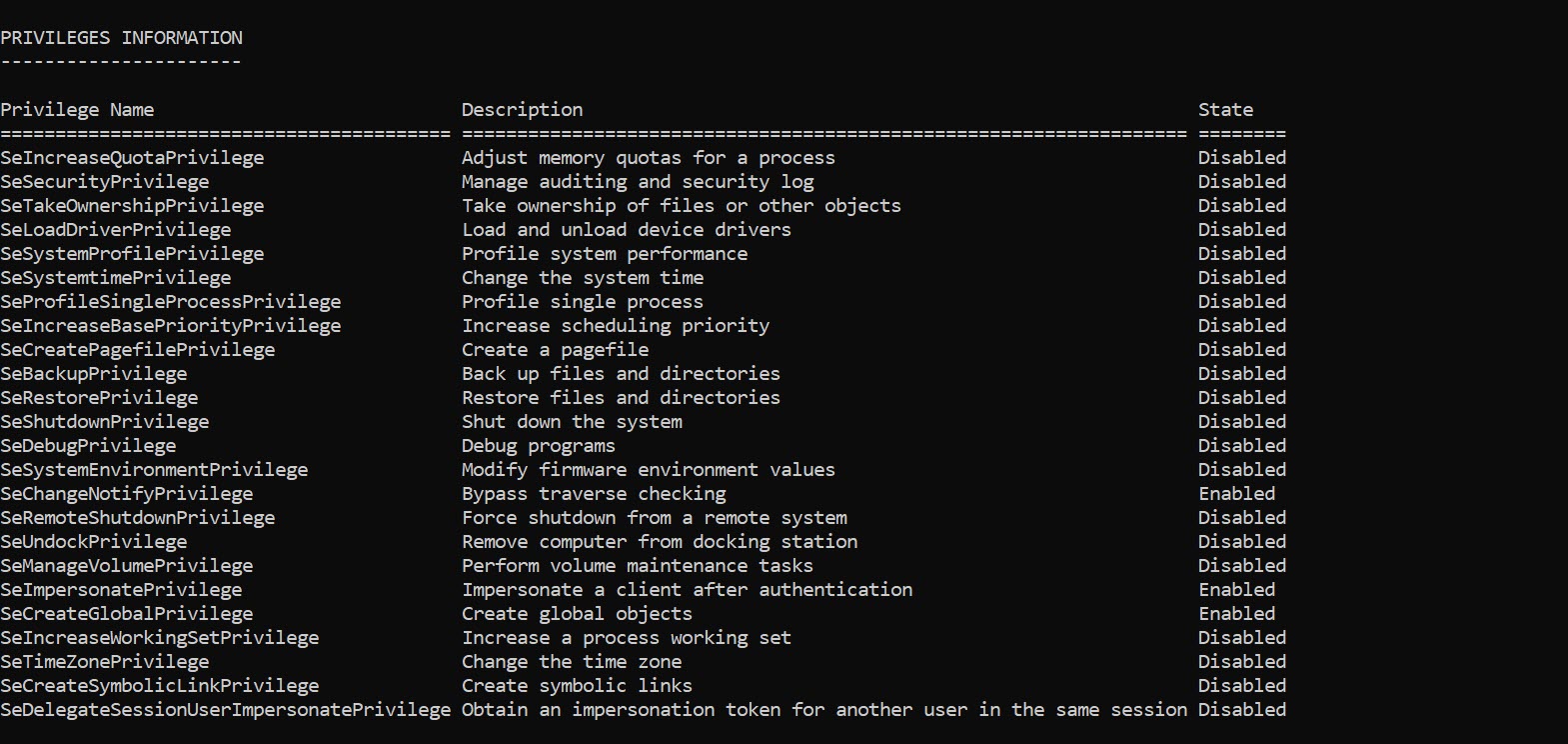
On Windows a privilege is the right of an account, such as a user or group account, to perform various system-related operations on the local computer. There are 36 privileges defined in the Privilege Constants although a number are used internally by the operating system. There are a number of privileges that are considered game over, in… Continue reading Game Over Privileges
Advanced socat
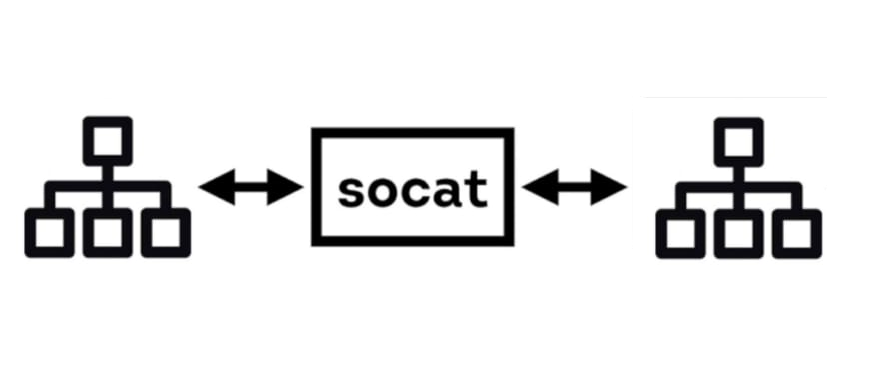
socat is a general-purpose networking tool that allows the creation of two bidirectional streams. It has a large amount of support for different protocols and data sources, including OPENSSL, SOCKS4, TCP, UDP, TAP, SCTP and more. When performing a penetration test this tool can be leveraged to bypass basic firewall restrictions and transfer files across… Continue reading Advanced socat
Making a PoC for CVE-2020-0668
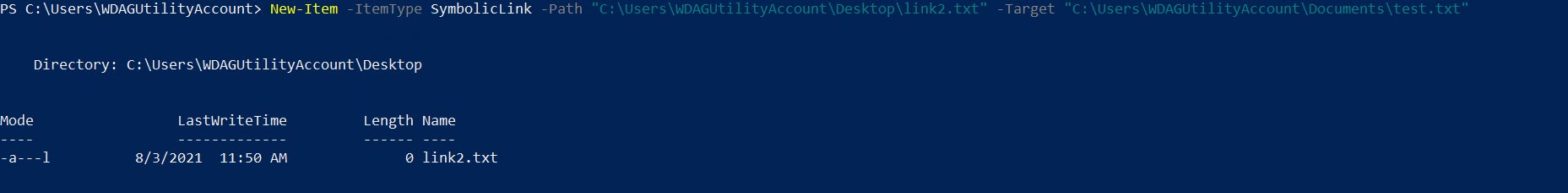
Recently Clément Labro released a blog post about an arbitrary file move vulnerability he discovered. This was CVE-2020-0668 which involved abusing Service Tracing to cause an arbitrary file move with the help of symlinks. I confirmed the vulnerability using the Google Project Zero symboliclink-testing-tools but wanted to create a standalone executable, that could be easily shipped to a… Continue reading Making a PoC for CVE-2020-0668